
Getty Photos
Crooks are working additional time to anonymize their illicit on-line actions utilizing 1000’s of units of unsuspecting customers, as evidenced by two unrelated studies printed Tuesday.
The primary, from safety agency Lumen Labs, studies that roughly 40,000 house and workplace routers have been drafted right into a prison enterprise that anonymizes illicit Web actions, with one other 1,000 new units being added every day. The malware accountable is a variant of TheMoon, a malicious code household courting again to a minimum of 2014. In its earliest days, TheMoon virtually solely contaminated Linksys E1000 sequence routers. Through the years it branched out to concentrating on the Asus WRTs, Vivotek Community Cameras, and a number of D-Hyperlink fashions.
Within the years following its debut, TheMoon’s self-propagating conduct and rising potential to compromise a broad base of architectures enabled a progress curve that captured consideration in safety circles. Extra not too long ago, the visibility of the Web of Issues botnet trailed off, main many to imagine it was inert. To the shock of researchers in Lumen’s Black Lotus Lab, throughout a single 72-hour stretch earlier this month, TheMoon added 6,000 ASUS routers to its ranks, a sign that the botnet is as robust because it’s ever been.
Extra gorgeous than the invention of greater than 40,000 contaminated small workplace and residential workplace routers situated in 88 international locations is the revelation that TheMoon is enrolling the overwhelming majority of the contaminated units into Faceless, a service offered on on-line crime boards for anonymizing illicit actions. The proxy service gained widespread consideration final yr following this profile by KrebsOnSecurity.
“This international community of compromised SOHO routers offers actors the power to bypass some commonplace network-based detection instruments—particularly these based mostly on geolocation, autonomous system-based blocking, or these that target TOR blocking,” Black Lotus researchers wrote Tuesday. They added that “80 p.c of Faceless bots are situated in the US, implying that accounts and organizations inside the US are major targets. We suspect the majority of the prison exercise is probably going password spraying and/or knowledge exfiltration, particularly towards the monetary sector.”
The researchers went on to say that extra conventional methods to anonymize illicit on-line conduct could have fallen out of favor with some criminals. VPNs, for example, could log person exercise regardless of some service suppliers’ claims on the contrary. The researchers say that the potential for tampering with the Tor anonymizing browser may additionally have scared away some customers.
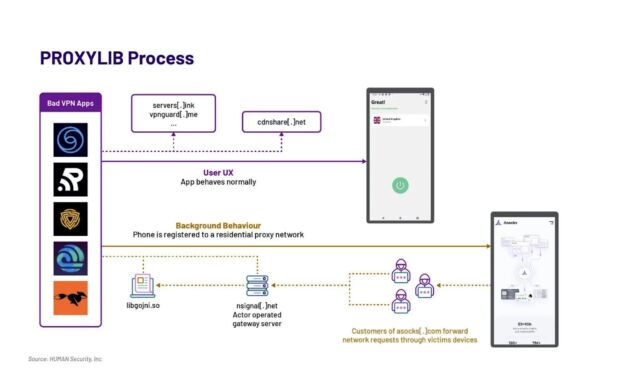
The second publish got here from Satori Intelligence, the analysis arm of safety agency HUMAN. It reported discovering 28 apps obtainable in Google Play that, unbeknownst to customers, enrolled their units right into a residential proxy community of 190,000 nodes at its peak for anonymizing and obfuscating the Web site visitors of others.
HUMAN
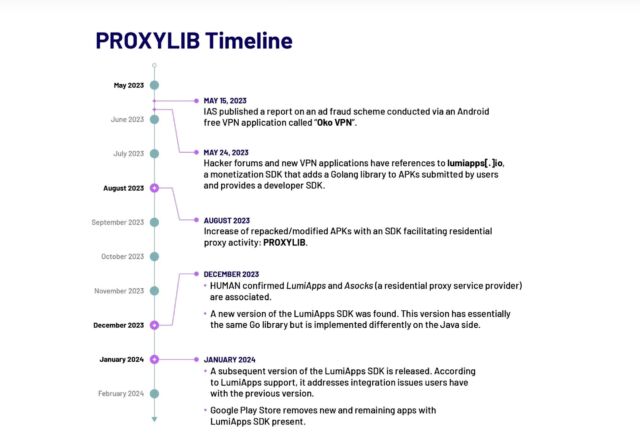
ProxyLib, the title Satori gave to the community, has its roots in Oko VPN, an app that was faraway from Play final yr after being revealed utilizing contaminated units for advert fraud. The 28 apps Satori found all copied the Oko VPN code, which made them nodes within the residential proxy service Asock.
HUMAN
The researchers went on to establish a second era of ProxyLib apps developed via lumiapps[.]io, a software program developer package deploying precisely the identical performance and utilizing the identical server infrastructure as Oko VPN. The LumiApps SDK permits builders to combine their customized code right into a library to automate commonplace processes. It additionally permits builders to take action with out having to create a person account or having to recompile code. As a substitute they’ll add their customized code after which obtain a brand new model.

HUMAN
“Satori has noticed people utilizing the LumiApps toolkit within the wild,” researchers wrote. “Many of the functions we recognized between Might and October 2023 look like modified variations of recognized official functions, additional indicating that customers don’t essentially must have entry to the functions’ supply code with a view to modify them utilizing LumiApps. These apps are largely named as ‘mods’ or indicated as patched variations and shared outdoors of the Google Play Retailer.”
The researchers don’t know if the 190,000 nodes comprising Asock at its peak had been made up solely of contaminated Android units or in the event that they included different kinds of units compromised via different means. Both manner, the quantity signifies the recognition of nameless proxies.
Individuals who need to stop their units from being drafted into such networks ought to take a couple of precautions. The primary is to withstand the temptation to maintain utilizing units as soon as they’re now not supported by the producer. Many of the units swept into TheMoon, for example, have reached end-of-life standing, that means they now not obtain safety updates. It’s additionally necessary to put in safety updates in a well timed method and to disable UPnP except there’s a superb purpose for it remaining on after which permitting it just for wanted ports. Customers of Android units ought to set up apps sparingly after which solely after researching the status of each the app and the app maker.

