Getty Photos
The US Treasury Division has sanctioned three Chinese language nationals for his or her involvement in a VPN-powered botnet with greater than 19 million residential IP addresses they rented out to cybercriminals to obfuscate their unlawful actions, together with COVID-19 assist scams and bomb threats.
The felony enterprise, the Treasury Division stated Tuesday, was a residential proxy service often called 911 S5. Such providers present a financial institution of IP addresses belonging to on a regular basis residence customers for patrons to route Web connections via. When accessing an internet site or different Web service, the connection seems to originate with the house consumer.
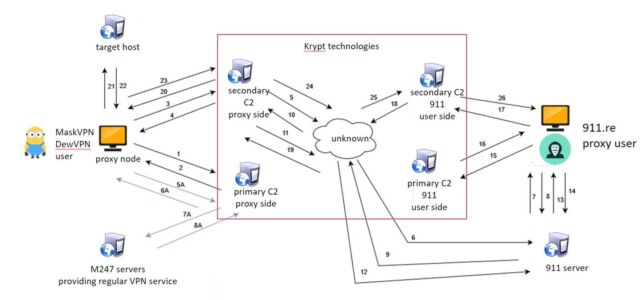
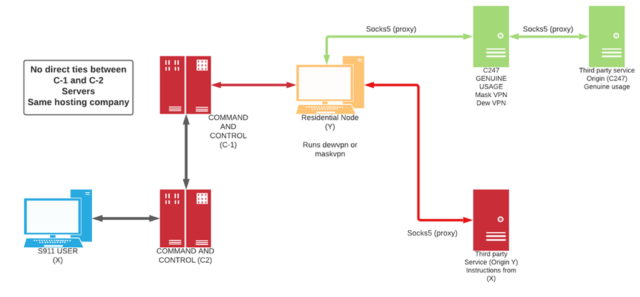
In 2022, researchers on the College of Sherbrooke profiled 911[.]re, a service that seems to be an earlier model of 911 S5. On the time, its infrastructure comprised 120,000 residential IP addresses. This pool was created utilizing one in every of two free VPNs—MaskVPN and DewVPN—marketed to finish customers. In addition to performing as a authentic VPN, the software program additionally operated as a botnet that covertly turned customers’ gadgets right into a proxy server. The complicated construction was designed with the intent of creating the botnet onerous to reverse engineer.
College of Sherbrooke
MaskVPN and DewVPN linked gadgets to the kind of server authentic VPNs use to obfuscate the originating IP handle and route site visitors via an encrypted tunnel. On the similar time, hidden performance established a everlasting TCP socket to a botnet command-and-control server. College of Sherbrooke researchers wrote:
This TCP connection is made to the C2 servers of the 911.re backend infrastructure and renders the node obtainable for connections via the 911.re interface. A heartbeat course of is in place to make sure the node is listed as obtainable. At no time, there’s direct connection between the contaminated node and the 911.re paid subscriber even when the node is chosen, and site visitors passes via. All of the community site visitors is at all times routed between the C2 servers which might be USA primarily based, lowering the chance of anomaly detection by IDS or IPS methods. Masks VPN and Dew VPN are utilizing a customized implementation of the open-source OpenVPN.
College of Sherbrooke
The analysis led to an investigation by KrebsOnSecurity that uncovered Yunhe Wang of Beijing as one of many people who registered domains utilized by the 911[.]re infrastructure.
Wang was one in every of three folks sanctioned on Tuesday. Treasury officers stated that Wang was the registered subscriber of providers used each by 911 S5 and the MaskVPN and DewVPN operations, a sign they have been counting on among the similar sources reporter Brian Krebs did. In addition they named Jingping Liu as a co-conspirator for allegedly serving to Wang launder digital forex and different proceeds generated from the 911 S5 enterprise. The officers additional named Yanni Zheng, for allegedly performing beneath the facility of legal professional for Wang and collaborating in enterprise transactions and making purchases and funds on Wang’s behalf, together with for a luxurious beachfront condominium in Thailand.
“These people leveraged their malicious botnet know-how to compromise private gadgets, enabling cybercriminals to fraudulently safe financial help meant for these in want and to terrorize our residents with bomb threats,” stated Beneath Secretary Brian E. Nelson. “Treasury, in shut coordination with our regulation enforcement colleagues and worldwide companions, will proceed to take motion to disrupt cybercriminals and different illicit actors who search to steal from US taxpayers.”
The treasury officers additionally sanctioned three Thailand-based companies: Spicy Code Firm Restricted, which bought extra actual property properties for Wang, and Tulip Biz Pattaya Group Firm Restricted and Lily Suites Firm Restricted, each of which have been bought by Wang.
The officers stated the 911 S5 botnet comprised roughly 19 million IP addresses. Criminals used it in “tens of hundreds of fraudulent purposes” associated to coronavirus reduction scams that resulted within the lack of billions of {dollars} to the US authorities. The IP addresses compromised by the service have been additionally linked to a collection of bomb threats made all through the US in July 2022.
Beneath the designations, all property of people and companies situated within the US or within the possession or management of US individuals should be blocked and reported to the Treasury Division’s Workplace of Overseas Belongings Management. The sanctions additionally prohibit dealings by anybody within the US involving any of the blocked property. Individuals who run afoul of the sanctions could themselves be uncovered to designation.
Tuesday’s motion comes six days after researchers from Google-owned safety agency Mandiant stated that the use by China-nexus menace actors of residential proxy networks often called operational relay field networks was hindering conventional technique of monitoring and defending towards cyberattacks. Mandiant researchers urged defenders to undertake new approaches.
“Mandiant asserts that the easiest way to rise to the problem posed by ORB networks is to cease monitoring espionage C2 infrastructure as an inert indicator of compromise and begin monitoring it as an entity with distinct TTPs,” the researchers wrote. “We not function on this planet of “block and transfer on” the place IPs are a part of APT’s weaponization and C2 kill chain section.”

